Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Nmap is a perfect scanning tool for hackers out there and boy..they use it extensively.Many systems and network administrators 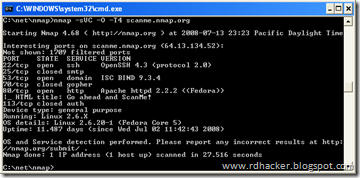
Here is how to do that
[1] Start by downloading the version of nmap from here . Net Tools also contain the NMAP scanner.
Windows users, install nmap by extracting the contents of the downloaded file to the C:\WINDOWS\system32 directory. Linux or Unix geeks can install nmap by extracting the source code to a directory, changing to that directory, and typing " ./configure ", "make", and "make install", all from a command-line terminal.
[2] Now Open a command terminal. On Windows, do this by going to
Start >Programs >Accessories> Command Prompt
On Linux, simply use the terminal open from when you installed nmap.
Change directories to where you saved nmap by typing: "cd [wherever you saved nmap]". You must enter it in a specific format or the command will not work. For instance, to change to My Documents, you would type:
cd C:\Users\Me\My Documents
[3] Run a simple ping scan, which will simply say "Hello! Are you connected? " to each computer you specify. Type
nmap -vv -sP [target]
The target can be a domain (www.microsoft.com), an IP address (127.0.0.1), a network (192.168.1.0/24), or a file containing any combination of the above. nmap will discover the IP address of the target if it wasn't given, and immediately ping the target, returning the results, which it prints to the screen.
[4] Lets Try a SYN Stealth scan. This type of scan will try to knock on all of the "doors" of the computer and see if anyone answers. To run a SYN Stealth scan, type
nmap -vv -sS [target]
The -sS switch tells nmap that we want a SYN Stealth scan. nmap will now get the IP address(es) as before, then ping the target to make sure that it is alive. However, instead of stopping there, nmap will now start asking to make a connection to the computer on each "door" or "port" that it has, 1-65535. When the computer opens the door, nmap tears down the connection and reports that the port is open. Once it is finished, it will report its results to you.
Run another SYN scan, but this time, add the " -oX target.xml " switch onto the end. This will output nmap's results to an XML file, viewable in any web browser. The only problem with this is that you need to hunt for the file if you placed it in your system32 directory.
Tips
- Is your target not responding? Then try adding the " -P0 " switch to your scan. This will force nmap to start the scan, even if it thinks that the target doesn't exist and this is useful if the computer is blocked by a firewall.
- Wondering how the scan is going? View nmap's progress by hitting the spacebar or any other key.
- If your scan is taking forever to complete (think twenty minutes or more), try adding the "-F " switch to the nmap scan to have nmap scan only the most frequently used ports.
Keep In Mind
- Make sure that you have permission to scan the target! Scanning www.FBI.gov is just asking for trouble. If you want a target to scan, try scanme.nmap.org. This is a test computer set up by the author of nmap, free to scan without getting yelled at. Or you can read the on how to save your ass from FBI
- If you frequently run nmap scans, be prepared to answer questions from your ISP (Internet Service Provider). Some ISPs routinely look for nmap traffic, and nmap isn't exactly the most inconspicuous tool. nmap is very well-known tool, and one that is used by hackers, so you may have a little explaining to do.
I hope that was informative.
Posted by XERO.WIKIHOW.ALL RIGHTS RESERVED.



